What would you do if sensitive information about national security was leaked online? This scenario recently unfolded when a cyber attack targeted the French defense contractor Naval Group, exposing details that could raise serious concerns for France and its allies. Let’s delve into the intricacies of this situation, what it means for cybersecurity, and how you can protect yourself and your data.

This image is property of blogapp.bitdefender.com.
The Incident: What Happened?
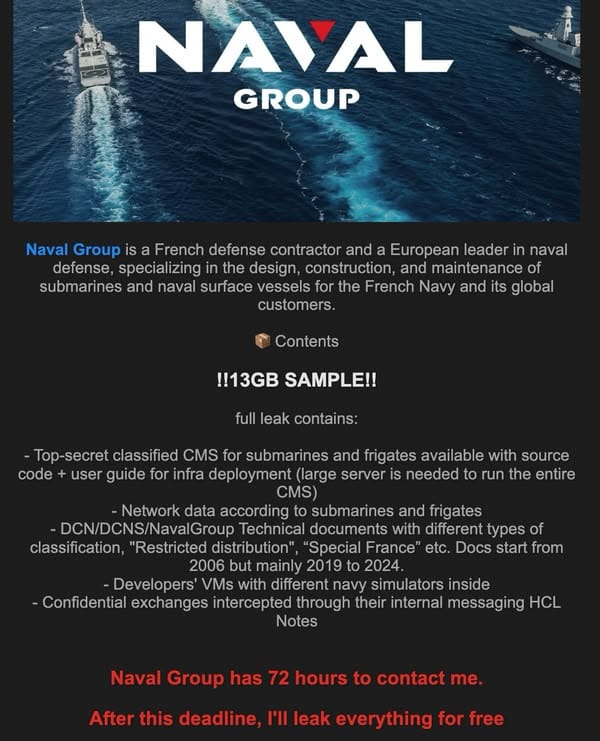
In July 2025, Naval Group found itself at the center of a significant cyber attack, resulting in what reportedly was approximately 1 TB of sensitive internal data being circulated online. The attacker, identifying themselves as “Neferpitou,” claimed to have access to critical information related to submarine systems, weapon software, and internal communications. This breach was announced on an underground hacking forum, which is not an uncommon method for hackers to showcase their exploits.
Who is Naval Group?
Naval Group is a significant player in the defense sector, particularly noted for constructing and maintaining ships and submarines for the French Navy. Their portfolio includes not just conventional vessels but also highly sophisticated nuclear submarines. Given its close ties with international clients like India and Brazil, a breach at Naval Group has implications that extend beyond French borders, potentially endangering the security of allied nations.
The Hacker’s Motive
The hacker, Neferpitou, made an unusual approach by offering a free 13GB sample of the data before threatening to release the full trove if a response wasn’t received within a specified time frame. It’s crucial to note that no ransom demand has been disclosed. This tactic showcases a growing trend among hackers, seeking not just monetary gain but also recognition within the hacking community.
This image is property of blogapp.bitdefender.com.
The Data Leaked
The implications of the leaked data are staggering. The contents include:
- Source code for combat systems utilized on French nuclear submarines and frigates.
- Software for various weapon systems.
- Simulation environments for training purposes.
- Detailed network designs essential for operational functionalities.
- User manuals and internal communication documents.
Significance of the Data
The type of information exposed could greatly affect the operational integrity of the French Navy. Having access to combat system code could allow potential adversaries to understand vulnerabilities. Conversely, it could also enable them to devise countermeasures against French military assets. Essentially, this kind of breach poses a grave risk to national security.
The Reaction from Naval Group
In response to the incident, Naval Group has stated that they are investigating the alleged breach with support from cybersecurity experts. They emphasized that, at least at that point, no direct intrusion into their IT environments was detected and that their activities had not been impacted. However, labeling the incident a “reputational attack” underscores the seriousness of the situation, as the trust of both the French Navy and international clients is at stake.

This image is property of blogapp.bitdefender.com.
Cybersecurity Implications
This incident is a stark reminder of the vulnerabilities that exist within even the most secure organizations. Cybersecurity is a constantly evolving field, and threats can come from various vectors.
The Threat Landscape
Recent warnings from Microsoft shed light on ongoing cyber threats, including vulnerabilities like the “ToolShell” exploit affecting SharePoint servers. While it’s currently unconfirmed whether Naval Group’s breach is related to this specific exploit, it highlights a broader trend: cybercriminals are becoming increasingly adept at taking advantage of software vulnerabilities.
Protecting Your Organization
Regardless of the industry, organizations must prioritize cybersecurity. Here are several steps you can take to enhance your defenses:
Regular Software Updates
Keeping software up to date is one of the easiest ways to protect against vulnerabilities. Software developers frequently release patches to fix security flaws. Making sure your organization implements these updates in a timely manner can help reduce the risk of breaches.
Employee Training
A significant percentage of data breaches occur due to human error. By training your employees on the basics of cybersecurity, like recognizing phishing attempts and securing personal devices, you create a more secure environment. Regular training sessions can reinforce this culture of awareness.
Implementing Strong Access Controls
Access controls ensure that sensitive information is only available to those who need it. This means enforcing strong password policies and regularly reviewing who has access to critical systems.
Utilizing Cybersecurity Tools
Investing in reliable cybersecurity solutions can help detect and mitigate potential threats before they become issues. Look for tools that offer comprehensive protection, including firewalls, antivirus software, and intrusion detection systems.

This image is property of blogapp.bitdefender.com.
State-Sponsored vs. Private Hackers
While discussing cybersecurity threats, it’s essential to differentiate between state-sponsored attacks and those conducted by private hackers.
Characteristics of State-Sponsored Attacks
State-sponsored hacker groups typically have far greater resources and expertise at their disposal compared to independent hackers. Their objectives might include:
- Gathering intelligence
- Disrupting critical infrastructure
- Cyber espionage
These attacks can often be more sophisticated and targeted than those executed by independent hackers.
Independent Hackers
On the other hand, independent hackers or cybercriminals may focus on financially motivated attacks, such as stealing credit card information or deploying ransomware. They may also engage in hacktivism, which expresses political opinions through cyber means.

This image is property of blogapp.bitdefender.com.
Conclusion
The cyber attack on Naval Group is a clarion call for organizations everywhere. The complexities of modern cybersecurity demand that you remain vigilant, proactive, and informed about potential threats. Whether it’s understanding the importance of software updates or investing in robust cybersecurity tools, every action counts.
In a world where data and intelligence are paramount, the lessons learned from events like these cannot be overlooked. Organizations must adopt a comprehensive approach to cybersecurity, involving training, technology, and constant vigilance to ensure the safety of their systems and sensitive information.
As you ponder the implications of these types of breaches, consider what steps you can take to bolster your defenses against the ever-evolving threat landscape. The responsibility of protecting your data ultimately lies in your hands, and being proactive could very well mean the difference between a secure organization and one that falls victim to cybercriminals.