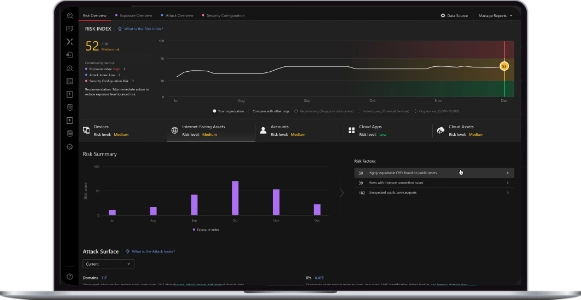
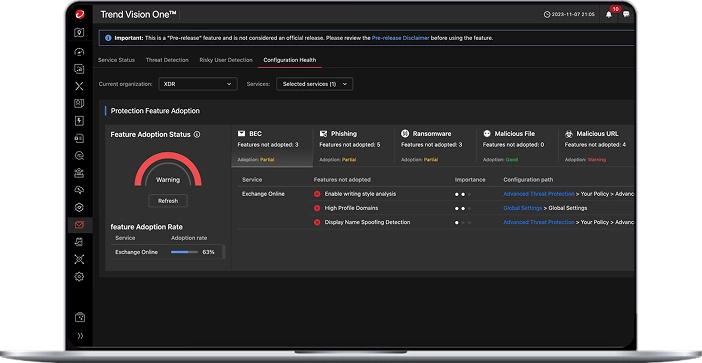
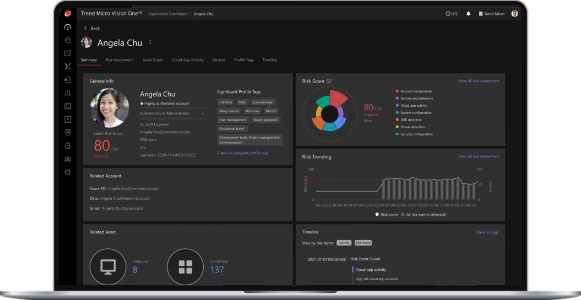
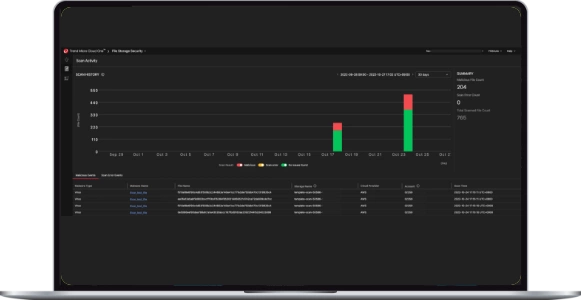
What would you do if a persistent threat to your systems emerged, potentially targeting critical infrastructure?
In today’s digital landscape, understanding and defending against threats like UNC3886 has become essential, especially considering their recent activities. By revisiting and analyzing their tactics, you can bolster your own defenses against ongoing and emerging risks.
This image is property of trendmicro.scene7.com.
Overview of UNC3886
An understanding of the threat landscape is crucial. UNC3886 stands out as a formidable Advanced Persistent Threat (APT) group known for targeting major segments of critical infrastructure. This includes telecommunications, government entities, technology firms, and defense sectors. Recently, they gained attention for their aggressive attack in Singapore, underscoring their capability and intent.
The Importance of Critical Infrastructure
Critical infrastructure is the backbone of society, enabling the functioning of essential services. Its disruption can lead to severe consequences, affecting everyday life, public safety, and national security. Hence, the actions of groups like UNC3886 shouldn’t be taken lightly. Their targeting of such sectors raises alarms and calls for strategic defenses.
Exploitation Focus
Understanding how UNC3886 exploits vulnerabilities is critical in formulating your defense strategies. They are particularly noted for their swift actions against zero-day vulnerabilities and critical issues.
Zero-Day Vulnerabilities
Zero-day vulnerabilities are software flaws that are unknown to the program’s developers and thus have no available patches for mitigation. When hackers discover these vulnerabilities, they can exploit them before any defenses can be enacted, making it essential to deploy robust security measures to identify and secure these weaknesses as quickly as possible.
Targeted Technologies
UNC3886 has a keen focus on network and virtualization devices. Notable among their targets are:
| Target Technology | Description |
|---|---|
| VMware vCenter/ESXi | Widely used for managing virtualized environments and critical applications. |
| Fortinet FortiOS | A security operating system that serves as a point of defense against external threats. |
| Juniper Junos OS | A network operating system providing fast and secure networking capabilities. |
Each of these technologies plays a crucial role in enterprise operations. Compromises here could lead to unauthorized access and control over vast networks.
This image is property of trendmicro.scene7.com.
Toolsets Utilized
When it comes to executing their attacks, UNC3886 employs a range of custom tools, showcasing their level of sophistication. Their toolset includes remote access and rootkit utilities, which aid in maintaining persistence within compromised environments.
TinyShell
TinyShell serves as a covert remote access tool that allows attackers to maintain control over the targeted systems discreetly. Deploying such tools makes detection challenging, as they often blend in with legitimate traffic and operations.
Reptile
Reptile is a stealthy Linux rootkit that can be used to hide various processes and maintain control over systems without raising alarms. Rootkits are particularly dangerous because they can manipulate system functionality while maintaining their presence undetected.
Medusa
Medusa integrates multiple capabilities for persistence and evasion. Its diverse functions allow the attacker to maneuver within a system, evade detection, and exploit new vulnerabilities as they arise. Understanding their toolsets provides valuable insight into defending against their methodologies.
Tactics for Defense
Now that you’re familiar with UNC3886’s capabilities, it’s time to shift the focus to defense. The group employs layered persistence and employs advanced defense evasion techniques to gain and maintain access to systems. Recognizing these tactics arms you with the knowledge necessary to safeguard your critical assets.
Layered Persistence
Layered persistence refers to the strategy of implementing multiple methods to establish a foothold in a target network. While removing one may not be sufficient to eradicate the threat, understanding this helps you prioritize defensive technology and procedures.
Here are some common tactics used by UNC3886:
| Tactic | Description |
|---|---|
| Deployment of Rootkits | Utilize rootkits like Reptile to conceal their presence and maintain long-term access. |
| Living-off-the-land (LotL) Tactics | Leverage existing tools and environments rather than introducing new malware, making detection harder. |
| Backdooring/Replacing Core System Binaries | Modify essential system binaries to create backdoors while evading scrutiny. |
This image is property of trendmicro.scene7.com.
Strengthening Defenses
With insight into their tactics, you can adopt more robust defensive measures. It is crucial to approach these threats with a well-rounded security strategy.
Implementing Proactive Measures
To effectively mitigate risks from APT groups like UNC3886, consider these proactive measures:
-
Regular Software Updates: Continuously update software and systems to patch vulnerabilities. Scheduled updates ensure you stay ahead of potential exploits.
-
Threat Intelligence: Leverage threat intelligence feeds to understand emerging tactics, techniques, and procedures (TTPs) used by attackers. Staying informed helps develop proactive defenses.
-
Incident Response Plans: Establish and test incident response plans specific to potential APT engagements. Being prepared for an attack enhances your resilience.
-
User Education: Conduct regular training sessions for employees on recognizing phishing attempts and other social engineering tactics. An informed workforce is a vital line of defense.
-
Network Segmentation: Implement network segmentation strategies to isolate critical systems and reduce movement opportunities for unauthorized users.
Leveraging Advanced Security Solutions
With the tactics and toolsets used by UNC3886 in mind, you can enhance your overall security posture.
Intrusion Detection and Prevention Systems (IDPS)
Investing in IDPS can significantly bolster your defenses. These systems actively monitor network and system activities for malicious actions. Implementing this layer allows for early detection and response to unauthorized attempts to access your infrastructure.
Endpoint Detection and Response (EDR)
EDR solutions provide real-time monitoring and detection of threats across all endpoints. By adopting such technologies, you gain the ability to spot unusual behaviors and respond promptly, mitigating the impact of attacks.
Behavior Analytics
Utilizing user and entity behavior analytics (UEBA) systems can help in the detection of anomalies that standard security measures may overlook. These systems analyze typical patterns and identify unusual behavior that may indicate an ongoing attack.
Emphasizing the Human Element
While technology is vital in maintaining security, the human element remains equally important. Cultivating a security-aware culture within your organization enhances defenses tremendously.
Building a Security Culture
-
Encourage Open Communication: Create an environment where employees feel comfortable reporting suspicious activities without fear of repercussions. Transparency can significantly reduce response times.
-
Regular Training Sessions: Routine cybersecurity training keeps security present in everyone’s minds. Realistic simulations can demonstrate the importance of vigilance.
-
Recognizing and Rewarding Good Practices: Engage employees by recognizing their adherence to security protocols. Incentivizing good behavior reinforces a culture of security.
This image is property of trendmicro.scene7.com.
Conclusion
In a world where advanced threats like UNC3886 are ever-present, understanding their tactics and strengthening your defenses are key priorities. By focusing on proactive measures, leveraging technology effectively, and fostering a security-oriented culture, you can make significant strides in protecting your critical infrastructure.
As you move forward, consider these strategies as essential steps in your journey. Staying informed, updating your defenses, and fully engaging your workforce will fortify your organization and ensure you’re not just reacting to threats but actively working to prevent them. The challenges posed by persistent threats like UNC3886 are complex, but with the right approach, you can confidently defend against them.