What would you do if your personal data became the target of a massive cyberattack? Cybersecurity threats are becoming increasingly common, affecting even the largest corporations. Recently, Nokia allegedly faced a major data breach that has raised alarms in the cybersecurity community.

This image is property of blogger.googleusercontent.com.
Understanding the Breach: What Happened?
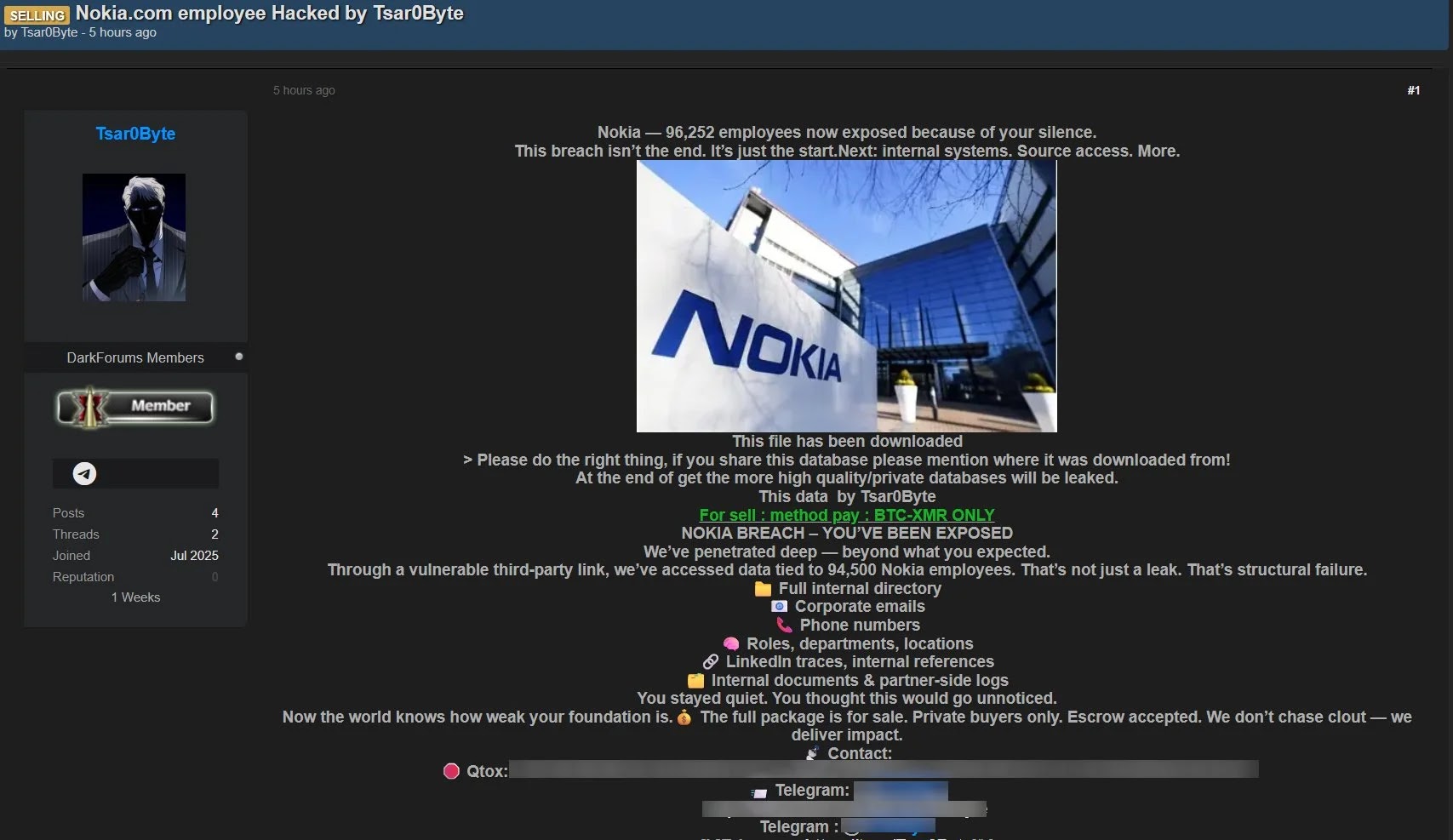
The threat actor known as Tsar0Byte has reportedly claimed to have gained access to Nokia’s internal network. This breach is particularly concerning as it exposed sensitive information about more than 94,500 employees. Imagine the stress this could cause if you were one of those employees. Suddenly, your private information is out in the wild, and the potential fallout can be overwhelming.
Allegations on Dark Web Forums
Following the alleged breach, Tsar0Byte took to dark web forums, including DarkForums, to lay claim to their findings. They reported accessing a trove of data, providing a chilling glimpse into what was compromised. Understanding the details of this breach helps you appreciate the risks involved with data security.
Sensitive Data Exposed
The data reportedly includes:
- Full employee names
- Corporate email addresses
- Phone numbers
- Department information and job titles
- LinkedIn profiles and internal references
- Internal documents
- Employee identification numbers
This sort of information could be a goldmine for malicious actors planning phishing attacks or social engineering schemes. Knowing what was exposed allows you to assess the potential impact on yourself and your colleagues.
How Did This Happen?
The breach appears to have taken advantage of vulnerabilities in a third-party contractor’s systems that had direct access to Nokia’s infrastructure for operational purposes. This method is becoming alarmingly common among cybercriminals targeting reputable companies, which is something every professional needs to keep an eye on.
Exploiting Third-Party Vulnerabilities
Tsar0Byte allegedly gained initial access through these poorly secured contractor systems. A commonly exploited technique involves using default credentials or misconfigured access controls. Have you ever thought about the security of third-party vendors that your company works with? It’s a critical issue that often doesn’t get the attention it deserves.
Supply Chain Attacks: A Growing Concern
Supply chain vulnerabilities represent a significant area of risk. The incident with Nokia is not an isolated event; similar attacks have been seen across various sectors. It reflects a broader trend where attackers recognize that weak links in a supply chain can open doors to larger, more secure systems. Understanding this risk can change how you engage with external partners, pushing for stricter security measures.
This image is property of blogger.googleusercontent.com.
Nokia’s Response: What Are They Doing?
In the wake of the breach claims, Nokia’s cybersecurity team acknowledged the situation and is conducting a thorough investigation. They emphasized that their preliminary findings pointed to no direct compromise of their primary systems, although they are continuing to monitor the situation closely.
Investigation Insights
The ongoing investigation aims to ascertain whether or not the claims made by the threat actor hold any truth. Cybersecurity research often focuses on determining the extent of security flaws, especially concerning compromised credentials or vendor system vulnerabilities. As part of their public strategy, Nokia has also communicated its commitment to transparency and continuous improvement in security protocols.
Importance of Vigilance
It’s crucial for businesses, especially those handling sensitive data, to remain vigilant. Understanding the root causes of such breaches and acknowledging the risks are fundamental for preventing future occurrences. Each department can play a part in bolstering security by following recommended best practices.
Implications for Employees: What You Should Know
While Nokia has yet to confirm whether customer data was compromised, the exposure of internal employee information raises alarms about potential social engineering attacks. You should be particularly mindful of how this information can be misused.
Risks of Phishing and Social Engineering
The sensitive data that has been allegedly exposed can be particularly valuable for cybercriminals who devise targeted phishing campaigns. Employees’ corporate emails and personal details create opportunities for these attackers to impersonate trusted contacts. Being aware of this risk can empower you to be more cautious in your communications.
Protecting Yourself
To protect yourself, familiarize yourself with the signs of phishing attempts and social engineering tactics. This includes:
- Being skeptical of unsolicited emails that ask for personal or sensitive information.
- Verifying requests through official channels.
- Keeping personal information private and shared only with trusted sources.
Importance of Internal Training
Companies like Nokia often implement ongoing security training for their employees, which can be a valuable asset in protecting not just the organization but also individual employees. Engaging in regular training allows you to stay ahead of potential threats and understand how to react appropriately when faced with suspicious activity.
Enhancing Vendor Security: The Way Forward
The Nokia breach underscores the importance of rigorous vendor security assessments. As you review your own organization’s relationships with third-party vendors, consider what safeguards can be put in place to ensure their systems are secure.
Regular Audits and Assessments
Regular vendor assessments can help identify security weaknesses that could be targeted by attackers. These assessments include:
- Evaluating the security posture of contractors.
- Reviewing access permissions and controls.
- Regularly updating security practices based on evolving threats.
By holding vendors accountable for their security measures, you can help protect your organization from future breaches.
Embracing Zero-Trust Security Models
Adopting a zero-trust security model can significantly reduce the risks associated with third-party access. This model operates on the principle that no one, even those inside the organization, should be trusted by default. Here’s how this might look in practice:
| Security Principle | Implementation Example |
|---|---|
| User Verification | Implement multi-factor authentication |
| Least Privilege Access | Regularly review and limit access permissions |
| Continuous Monitoring | Use advanced analytics to detect anomalies |
This strategic approach can dramatically enhance the security landscape of your organization and provide an added layer of protection against breaches.
Lessons Learned from Nokia’s Incident
Cybersecurity incidents like the one involving Nokia are invaluable learning experiences. They illustrate the evolving landscape of threats that companies face today and underscore the heightened need for robust security measures.
Importance of Controlled Access
Understanding that many breaches occur due to weak points in controlled access is vital. In many cases, privileged access can be an easy pathway for attackers. Make sure your organization limits access to sensitive data and only provides it to those who truly need it.
Proactive Incident Response Planning
Another takeaway is the importance of having an effective incident response plan. Following an event, having a clear and structured response can significantly mitigate damage and restore confidence.
Here’s a basic outline of what an incident response plan might include:
| Incident Response Phase | Description |
|---|---|
| Preparation | Establishing policies and procedures for handling incidents |
| Detection and Analysis | Implementing systems that alert you to breaches |
| Containment and Eradication | Limiting the scope of the breach and eliminating the threat |
| Recovery | Restoring systems and processes to normal operation |
| Post-Incident Review | Analyzing the breach to prevent future occurrences |
Having a robust plan will help everyone in your organization know their responsibilities and ensure a quick and effective response.
Building a Culture of Security
Finally, building a culture of security within the organization is paramount. Every employee should be educated about their role in protecting sensitive company information. You should engage in open discussions regarding data security, encouraging staff to share insights and experiences, making everyone part of the protection strategy.
Conclusion: Staying Proactive
As the situation continues to unfold, staying updated is essential. Cybersecurity is not a static field; it evolves rapidly, presenting new challenges and threats. While no company can be 100% secure, understanding vulnerabilities and implementing strict security protocols can help significantly reduce risks.
It’s vital to stay aware of the repercussions of breaches like that of Nokia and to take action within your own organization. Whether you’re part of the management team or a general employee, everyone has a role in fostering a secure environment.
Make sure to discuss your concerns with your company’s security team and advocate for improvements where necessary. Keeping an open line of communication can lead to a stronger security posture for everyone involved.
Drawing from the lessons learned, your organization can take proactive steps to mitigate risks, protect sensitive information, and ultimately maintain the trust of employees and clients alike.