Have you ever wondered how secure the networks of major corporations really are? With the ongoing evolution of cyber threats, it’s essential to stay informed about the latest incidents and vulnerabilities that affect even the biggest names in technology. In light of recent events, let’s take a closer look at an alarming situation involving Nokia and the claims of a breach in their internal network.

This image is property of blogger.googleusercontent.com.
The Breach: Tsar0Byte’s Claims
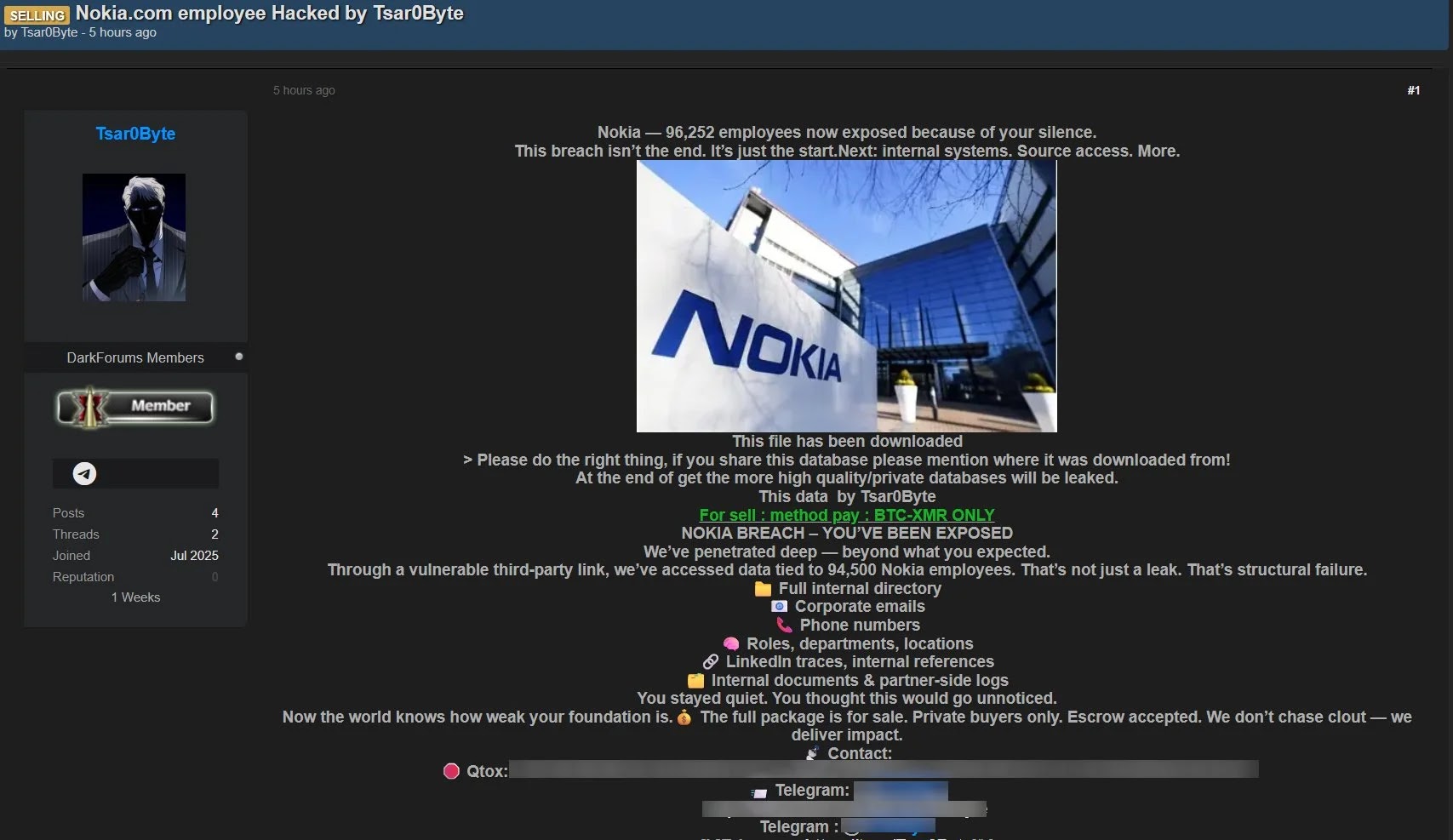
Recently, a threat actor known as Tsar0Byte has claimed access to Nokia’s internal network, revealing vulnerabilities that put a significant amount of sensitive employee data at risk. According to their assertions, these incidents highlight critical security concerns, especially when they involve third-party links that many companies rely on.
What Data Was Exposed?
The breach reportedly involves the exposure of sensitive data belonging to over 94,500 employees. Tsar0Byte boasted about having access to information such as:
- Full names and contact details of employees
- Corporate email addresses and phone numbers
- Department affiliations and job titles
- LinkedIn profiles and internal references
- Employee identification numbers
- Internal documents and partner logs
The gravity of this breach raises important questions about how such a significant amount of confidential information could be accessed.
The Method of Attack
According to cybersecurity researchers analyzing Tsar0Byte’s claims, the breach was likely initiated through compromised systems of a third-party contractor that maintained access to Nokia’s internal infrastructure. This breach is particularly concerning as it underscores a growing trend where cybercriminals exploit vulnerabilities in supply chains.
Supply Chain Vulnerabilities: A Growing Concern
Supply chain attacks have become increasingly common in recent years. More organizations depend on third-party vendors for various services, creating multiple entry points for potential threats. In this instance, Tsar0Byte may have taken advantage of:
- Poorly secured contractor systems: Companies sometimes overlook the security of their contractors. Misconfigured systems or default credentials can easily provide access to malicious actors.
- Less secure third-party vendors: Attackers often target vendors that have access to primary systems, leading to successful breaches of larger organizations.
As you can see, this incident reflects the critical need for companies to re-evaluate their vendor security practices.
Nokia’s Response
Nokia’s cybersecurity team has acknowledged the claims made by Tsar0Byte and is currently conducting a thorough investigation into the situation. While preliminary findings suggest that they have not identified direct compromises to their main systems, they are continuing to monitor the situation closely.
Ongoing Investigations in Cybersecurity
For cybersecurity teams, incidents like these serve as wake-up calls. Below are some key considerations for how Nokia and other organizations should direct their focus going forward:
- Continuous monitoring: Keeping an eye on network activity helps identify any unusual behavior associated with potential breaches.
- Thorough investigation: Engaging cybersecurity researchers and incident response teams ensures that comprehensive assessments are made.
- Public communication: Transparent communication about breaches can be crucial in maintaining trust and minimizing the impact on public image.
This image is property of blogger.googleusercontent.com.
Implications of the Data Exposure
While Nokia has not confirmed whether customer data was directly affected by this breach, the implications of exposing internal employee information can lead to several potential risks, including:
Targeted Phishing Campaigns
With sensitive employee details publicly accessible or sold on the dark web, cybercriminals can tailor phishing attacks more effectively. They may impersonate trusted sources to extract even more sensitive data or instigate illicit transactions.
Social Engineering Attacks
Armed with knowledge regarding a company’s internal hierarchy and employee roles, attackers can execute social engineering attacks by exploiting trust. They could potentially manipulate employees into revealing sensitive information or providing access to secure systems.
Impact on Company Culture and Trust
Such breaches can create a sense of insecurity among employees, adversely affecting morale. In an era where security is paramount, retaining employee trust hinges on effective risk management and transparent communication strategies.
Enhancing Security Posture
In light of these incidents, how can organizations bolster their security posture to prevent future breaches? Below are a few strategies worth considering:
1. Strengthen Vendor Security Assessments
Evaluating third-party vendors is critical. Companies should:
- Conduct regular security assessments.
- Ensure vendors adhere to best practices and compliance standards before granting them access to internal networks.
2. Implement Zero-Trust Security Models
Adopting a zero-trust approach helps in mitigating risks associated with unauthorized access. This model emphasizes:
- Verification of every device and user, regardless of whether they are inside or outside the network.
- Continuous monitoring of user access for any anomalies.
3. Routine Audits of Access Privileges
Regular audits ensure that only the necessary personnel have access to sensitive information. To implement an effective auditing strategy, consider:
- Regularly reviewing user permissions.
- Revoking access for inactive or terminated employees.
- Keeping access privileges limited to the minimum required for specific roles.
Key Takeaways
In conclusion, the claims made by Tsar0Byte regarding Nokia’s internal network expose vulnerabilities that highlight crucial areas for improvement in cybersecurity practices. Here are some significant takeaways from this incident:
- Understanding supply chain risks: Recognize and address vulnerabilities in third-party systems.
- Proactive cybersecurity strategies: Engage in continuous monitoring and improvements.
- Influence on employee behavior: Understand the potential impact of data breaches on employee trust and company culture.
As cyber threats continue to evolve, it’s essential to keep up with advancements in security technologies and strategies that prioritize both employee and customer data protection.
The Future of Cybersecurity
Looking ahead, the landscape of cybersecurity will undoubtedly face new challenges and revelations. With rapid technological advancements, organizations must remain vigilant to navigate the complexities of ensuring secure operations.
Trends to Watch
As organizations work to fortify their defenses, some emerging trends include:
- Increased collaboration: Expect firms to collaborate more closely with security firms and law enforcement to share intelligence on emerging threats.
- Advancements in AI: Artificial intelligence might play a growing role in threat detection and response mechanisms.
- Enhanced employee training: Companies will likely invest in training their employees on security best practices to create a culture of proactive cybersecurity awareness.
Conclusion
In the wake of high-profile breaches like that of Nokia, staying updated on cybersecurity trends and best practices has never been more critical. Strengthening security postures and adopting a proactive stance can significantly reduce the risk of future incidents. By fostering a culture of awareness and introducing innovative strategies, companies can work towards creating safer digital environments for everyone involved.
As you think about the state of cybersecurity, consider the role you play in maintaining vigilance, whether as an individual, a part of an organization, or a member of a community. Together, we can contribute to a more secure future.